Estimated read time: 3-4 minutes
This archived news story is available only for your personal, non-commercial use. Information in the story may be outdated or superseded by additional information. Reading or replaying the story in its archived form does not constitute a republication of the story.
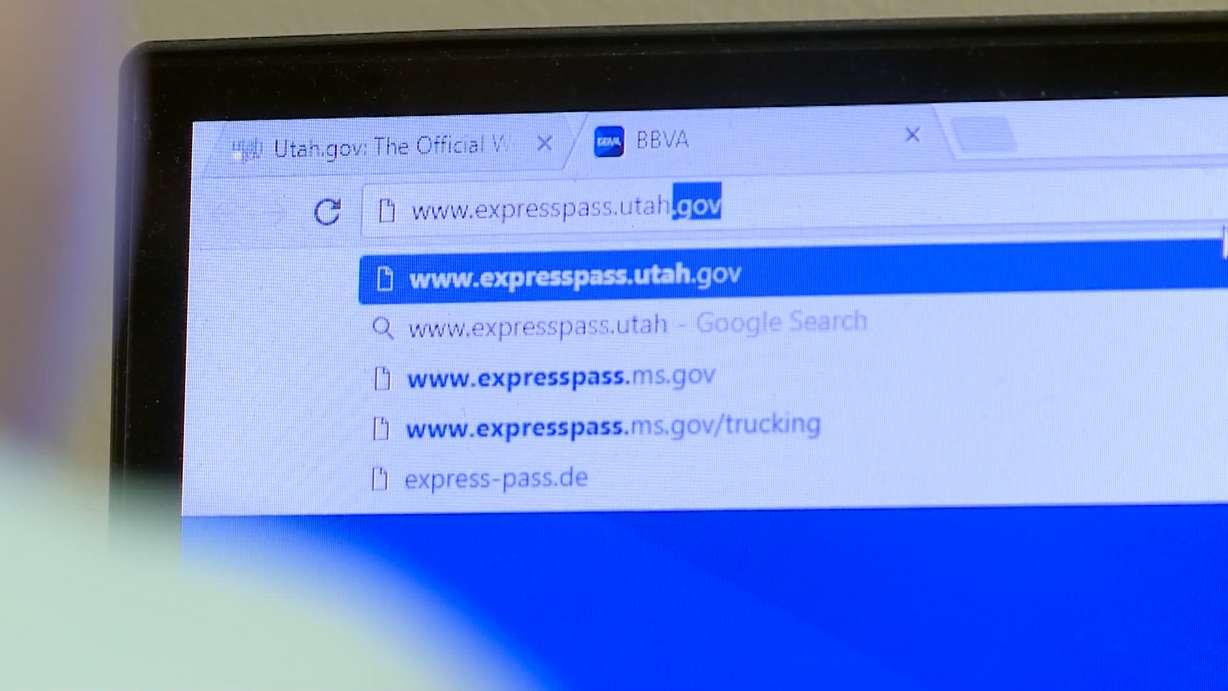
SALT LAKE CITY — State IT workers shut down a website Tuesday that was used to manage UDOT Express Pass accounts after they learned the personal information attached to as many as 21,000 accounts was readily accessible after a few simple steps.
Utah Department of Technology Services spokesperson Stephanie Weteling said it was unclear how long the vulnerability had existed within the site, expresspass.utah.gov, or whether anyone with ill intent had accessed the information, which included full names, addresses, phone numbers, emails, partial credit card numbers and card expiration dates.
Tyler Fitts, who works in the information technology field, discovered the flaw while encountering troubles entering a new password for his account.
“I went to the website and put my PIN number in — or my Express Pass number — and it said that an email would get sent to my address, and it actually showed my email address,” Fitts said. “I knew that’s a little bit bad to give information that you haven’t authenticated.”
After further investigation, Fitts discovered when he simply entered his Express Pass number and hit the Enter button, he could see all of his personal information in the code of the request that shows up in the Developer Tools tab on Google Chrome.
“Then, obviously, all I had to do was change one number and get someone else’s information,” Fitts explained. “I started at number one, and it worked, and I tried ’13,000,’ and it worked, and pretty much everything in between.”
UDOT spokesman John Gleason said the site managed the accounts of 16,000 active users and contained the information of 4,000 to 5,000 inactive or closed accounts.
Weteling said a new outside vendor identified as ETAN Industries took control of the site, in a change that occurred about a month ago.
Attempts to reach the company for comment Tuesday afternoon had not been met with a response as of late Tuesday night.
Weteling said the department was “concerned” by the flaw and was working to assess it and fix the problem.
“It is offline and will stay down until the issue has been resolved, and we understand what’s going on,” Weteling said.
A KSL staffer who learned of the flaw from Fitts entered randomly selected Express Pass numbers into the website before it was shut down, and came up with the address of a property associated with Salt Lake City-based attorney Steven Linton.
Linton said he, too, was concerned about the vulnerability.
“The fact that it’s my full name, my address and portions of my credit card all in one place—yeah, that’s a problem,” Linton said. “It seems like the state should be very careful about things like this, if anyone would be.”
Weteling said that numerous security policies and processes are expected to be met by vendors.
“We have a robust security team with the Department of Technology Services who are monitoring everything 24 hours a day, seven days a week,” Weteling said. “We’re on top of monitoring everything that comes in and out of the network.”
It was unclear as of Tuesday afternoon when the website would be brought back online.
Several bad outcomes could have resulted from the flaw, Fitts said, including someone potentially creating a fake Express Pass website resembling the original, and then using the personal information to phish for additional details from users such as passwords and credit card numbers.
Fitts noted the same steps he took on Google Chrome could have been done on most web browsers.
He said he believed significant changes should be considered, even perhaps with the business relationship with the vendor itself.
“It’s, like, reckless and incompetent for sure,” Fitts said. “Security stuff like this is not hard to do right these days.”