Estimated read time: 3-4 minutes
This archived news story is available only for your personal, non-commercial use. Information in the story may be outdated or superseded by additional information. Reading or replaying the story in its archived form does not constitute a republication of the story.
SALT LAKE CITY — A new piece of malware has been uncovered by Russian computer security firm Kaspersky which has been stealing data from high-level government and scientific computers and phones for the last five years, completely undetected. And it's still going.
The malware, dubbed Red October, is capable of stealing confidential files, including files that have been encrypted or even deleted from a device like a computer, flash drive or phone It also looks for files that use encryption styles favored by NATO as well as other European states.
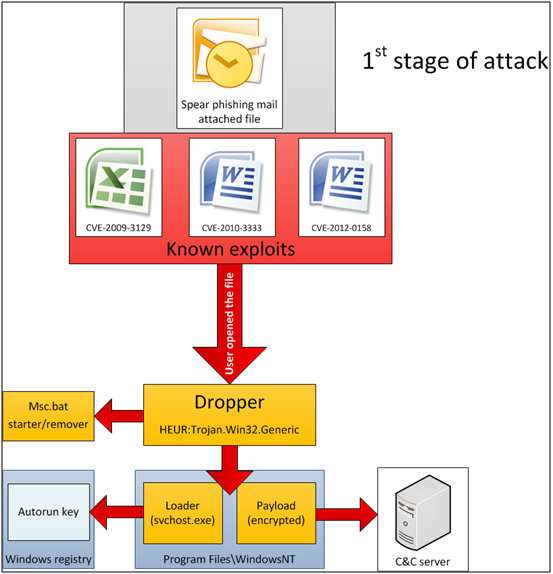
The malware has been using four well-known security vulnerabilities.
"The main purpose of the operation appears to be the gathering of classified information and geopolitical intelligence, although it seems that the information gathering scope is quite wide," the researchers said in their analysis. "During the past five years, the attackers collected information from hundreds of high profile victims although it's unknown how the information was used."

Kaspersky, a company which provides security software and consulting services, has said that there are hundreds of infections across the globe, including at least six in the United States.
That might not sound like much when compared to viruses and malware that infect millions of computers. The difference is that every infection of Red October is on a computer or phone owned by a high-level diplomat, scientist or government official who were likely specifically targeted.
The malware is also capable of "hiding" once it is discovered, according to Vitaly Kamluk, a malware researcher for Kaspersky.
"If it's discovered, it hides. When everyone thinks the coast is clear, you just send an email and 'boof' it's back and active again," he told the BBC.
Hundreds of terabytes of information have been stolen by Red October since 2007, but no one is sure who created the virus. It uses methods that are Chinese in origin, but the code itself contains Russian slang words. Russia is a likely origin, given the slang and some other technical details in the code that are typically used to accommodate Cyrillic characters.
But of course, any indicator could be a cover, intended to misdirect those trying to track down the origins of the malware.
Kaspersky has been working with US-CERT, a cyber-security arm of the United States, as well as several other international cyber-security organizations, during the course of the investigation, which began in October of 2011.
The highest rate of infection was in the Russian Federation as well as Eastern Europe, mostly focused on former Soviet states. But the actual number of infections is not known. Data currently available only comes from computers running Kaspersky software, so there may be hundreds more than currently found.
Though the malware has been compared to the the state-sponsored viruses like Flame and Stuxnet, Red October has an entirely novel architecture, and does not appear to be closely related to any known piece of malicious code. It does, however, use at least four well-known vulnerabilities in Microsoft Word and Excel files, as well as Java, which has recently come under fire due to vulnerabilities in the latest release.
The virus originally spread by being carried through person-specific emails written to personally appeal to the person they were sent to. An attachment would be opened and then the malware would get to work. It is also capable of infecting Windows phones, iPhones and Nokia phones and stealing intelligence from them.